With almost all developers (92%) using or experimenting with AI coding tools, AI continues to transform …
Technical knowledge is siloed and lives in the mind of a few key devs, causing them to spend their time an…
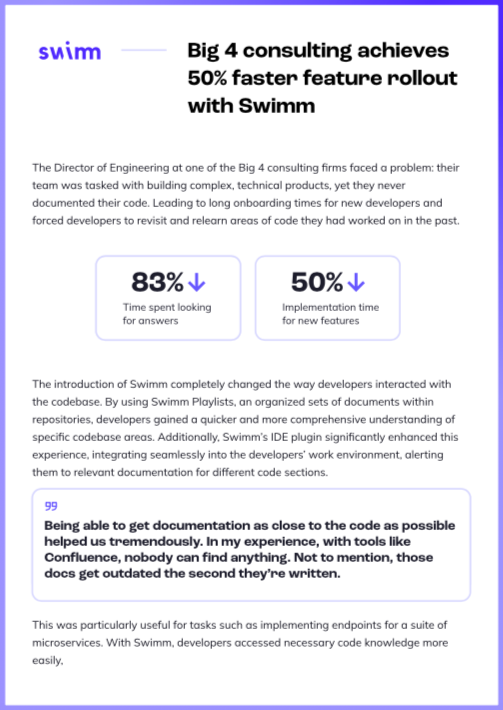
The Director of Engineering at one of the Big 4 consulting firms faced a problem: their team was tasked wi…
We all know there’s work to be done to ensure all identities and perspectives are valued in the workplace,…
Azul Platform Prime is the world’s fastest, most scalable, and most efficient JVM. An enhanced version of…
Azul, provider of the Java platform for the modern cloud enterprise, is the only company 100% focused on …
Azul’s highly trained support engineers have extensive Java experience and deep knowledge of the JVM, mem…
Ad hoc professional services are designed to provide customers with a wide range of assistance for the var…
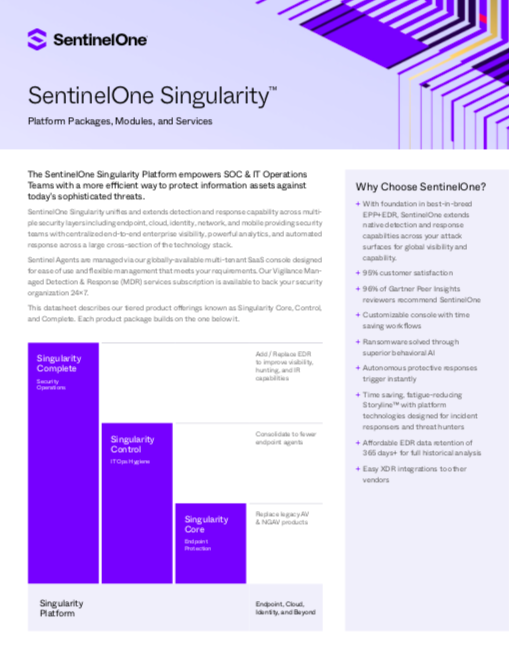
SentinelOne Singularity unifies and extends detection and response capability across multi- ple security …
The challenge of gaining visibility into all assets with sufficient context has hindered IT and security …
Chief Information Security Officers face an increasingly difficult set of responsibilities. They need cle…
By seamlessly integrating with over 750+ security and IT management technologies, Axonius Cybersecurity A…
In the landscape of ever-evolving security challenges, EliteOps introduces the Sprint program, an initiat…
At EliteOps, we stand out with our specialized, streamlined approach, breaking away from the generalized,…
Paycor is a human capital management company that provides HR and payroll technology to small and medium-…
Honeywell relied heavily on their channel partners for business growth and prospecting. They were looking…
New York Bariatric Group (NYBG) is an expert team of bariatric surgeons who provide surgical and non-surg…
Artificial Intelligence was created to make life easier. The technology completes tasks, quickly and effi…
This e-book provides a comparative look at how endpoint security solutions performed in the most recent AT…
As the demand for cyber insurance increases, so does the pricing and red tape. Discover how these challen…
In the realm of our highly connected world, the significance of cybersecurity has reached unparalleled hei…
senhasegura is a cybersecurity leader, specializing in Privileged Access Management (PAM) solutions that a…
Organizations often lack the capacity, resources, and expertise to properly identify and remediate supply…
Cybersecurity is more than detecting maliciousness. Frankly, the typical organization has a plethora of to…
ThreatLocker® is a Zero Trust endpoint protection platform that provides enterprise-level cybersecurity to or…
Supercharge Your Anti-Phishing Defense with PhishER Plus.
In this ebook, you’ll find relevant information to help you with the following questions: What should you be…
Old-school security awareness training doesn’t hack it anymore. Today, your employees are frequently exposed …
Report SummaryDevices running ThreatLocker® vs. not running ThreatLocker® 206 out of 42,000. To capture a com…
Routing data to the right tools and destinations gives you the flexibility to optimize your observability…
This solution guide provides a holistic view of the Cribl solution, and how it enables open observability…
All data has value, but not all at once. Today’s excess data may be exactly whatyour company needs later t…
The promise of quantum computing is tantalizing. Once quantum machines become sufficiently powerful, tasks…
In a world where everything is connected and nothing is trusted, public key infra- structure (PKI) is the …
PlayPlay helps Heifer International create more videos to engage its communities. Both for Internal Co…
Everywhere you look, there are videos competing for attention–on social media feeds, web browsers, on giant s…
In today's digital landscape, the role of a Chief Information Security Officer (CISO) is becoming more and …
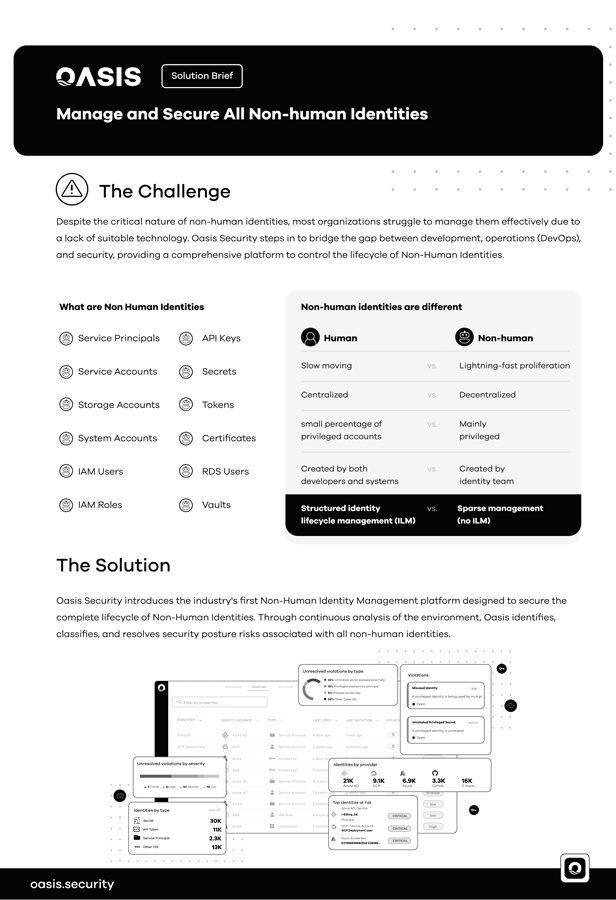
Despite the critical nature of non-human identities, most organizations struggle to manage them effectively d…
Application Allowlisting denies all applications from running except those that are explicitly allowed. This …
Revisit the Basics to Learn How A Different Approach Can Prevent More Attacks
Microsoft Windows Servers have been the fundamental basis of small and large business networks since the ear…
Many organizations utilize security testing (a.k.a penetration testing) to validate the security posture of t…
Ransomware is blackmail: an extortion proposition where bad actors seek to monetize hijacked data from an org…
Traditional vulnerability management approaches can no longer keep up with today’s dynamically changing busin…
Public key infrastructure (PKI) isn’t anything new. It’s been around for decades. Beginning as the trust engi…
The need for Crypto-Agility: How to know when your cyber security is past its expiration date.
Ready or not, the quantum era is coming. Protect your digital assets, applications, and infrastructure with c…
When your IT infrastructure resides in an enterprise data center, at the network edge, and in remote and bran…
Today’s digital economy has fundamentally transformed the pace and expectations of IT operations teams charge…
Operating and managing complex IT environments, particularly hybrid clouds, becomes time-consuming and costly…
How cloud-based technologies are impacting enterprise infrastructure, operations, and strategies.
Tracking customer experience (CX) metrics is essential for organizations aiming to understand their audiences…
In today’s experience economy, brands win or lose by their ability to deliver contextual and compelling perso…
With the rise of digital transformation and the growing number of channels that marketing teams support, tech…
Most security testing programs, particularly penetration testing, are compliance driven and performed once or…
Accelerate the FedRAMP process from 18 months to 3* and reduce preparation time by 50 - 60% with RegScale’s u…
Wiz partnered with RegScale to unite its new best-in-class cloud security posture management system with RegS…
What you need to know to prepare and recover from a ransomware attack.
The vendor landscape for security awareness training (SAT) is as diverse as it is innovative. This market has…
Picture this: you're scrolling through social media and you come across a video of a celebrity doing somethin…
Alarm bells are sounding off in College Park, Maryland.According to a recent study, researchers doubt it will…
The cloud landscape has grown significantly over the past decade due to which many organizations are making t…
How a Multinational Pharmaceutical Company Uses Cyera to Improve Data Security and Compliance
How Cyera Helped a Mortgage Lender Secure and Manage Sensitive Data
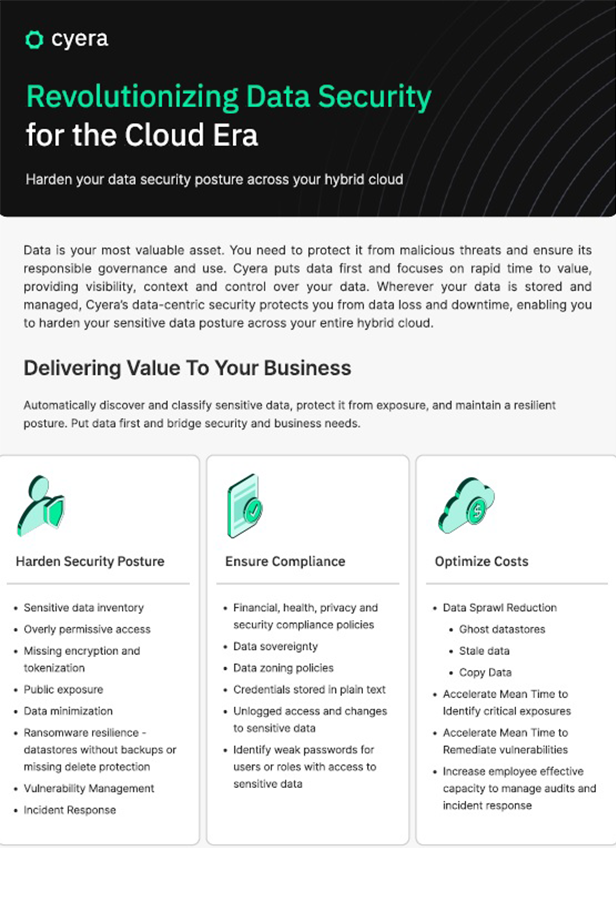
Harden your data security posture across your hybrid cloud. Cyera puts data first and focuses on rapid time t…
Each day, Cybersixgill collects approximately 10 million intelligence items from the deep, dark, and clear we…
Cybersixgill’s intelligence feed reduces incident response times by 75%
How to Protect Critical Assets Through Systematic, Proactive Threat Intelligence.
Headquartered in New York, NY, Goldman Sachs is a leading global banking, securities, and investment manageme…
According to Bain & Company, 2023 M&A activity will be on par with or exceed the level of activity in…
Forward Networks industry-leading verification platform, Forward Enterprise, analyzes and verifies network be…
Protecting your data in AWS is your responsibility. Cohesity Data Protect delivered as a service running on A…
Data is at the center of every organization. From home, remote, and branch office locations to on-premises da…
Organizations worldwide are facing continued economic uncertainty that challenges expected outcomes. As predi…
Transforming your organization’s business and culture through IT leadership
How do you know if your company is truly innovative?
Innovation as the driving force for sustainability Sustainability is a societal initiative that aims for huma…
Drive better visibility across SecOps by taking control of your data.
Gaining control over observability and security data, like metrics, logs, and traces, is criticalfor today’s …
Metrics, events, logs, and traces contain critical information about your customers andoperating environment.
The increasing threat and impact of ransomware is not going to subside until we develop better strategies for…
Relentlessly Future Focused, so you can be too.
Do you really know how many applications employee have connected to your organization's Google Workspace acco…
Do you really know how many third-party applications have access to your GifHub repository?
Many security and IT teams are concerned about a substantial security gap in their data warehouses such as GC…
How CYE helps you understand the true cost of cyber incidents and remediation so you can optimize security bu…
How to strengthen your security posture and optimize security investments by assessing and prioritizing cyber…
Assess, quantify, and mitigate your cyber risk.
Recipes for a Secure Cloud
Find Your Path to Successful Cloud Expansion
Security Awareness Training (SAT) has long been a central approach for companies seeking to educate their emp…
According to a 2022 survey by Osterman Research, the majority of cybersecurity leaders do not have an effe…
Sika is a specialty chemicals company with a leading position in the development and production of systems an…
We take responsibility for every project from beginning to end, providing full visibility throughoutwith our …
Kubernetes is the de facto standard for container orchestration. While good practice, image scanning alone is…
Server/VM Workload Detection & Response, part of the Singularity Cloud family, defends workloads running …
Digital transformation is more than a buzzword. It’s the process of evolving from rigid, legacy on-premises p…
Despite some time in the limelight as an overused buzzword, zero trust, for many organizations, has emerged a…
A multinational investment and financial services company, providing services to customers across more than 5…
Digital transformation has reshaped the world, improving the way businesses interact with customers, workers,…
Cyberattacks are inevitable—and nation-state and ransomware attackers are savvier than ever in “living off th…
Despite the deployment of PAM and MFA solutions, Illusive discovers privileged identity risks on 1 in every 6…
Illusive discovers and mitigates privileged identity risk policy violations that are exploited in all ransomw…
lllusive continuously discovers and automatically mitigates privileged identity risks and policy violations t…
Illuminating identity risks that leave every organization vulnerable to attack